


Thremo is designed to offer a different approach to how security is handled in software projects.
Thremo's main goal is to offer a software based security expert at a low cost, making IT security accessible to teams and projects of any size.
Security is easier to implement when thought about from the get-go. Thremo can be used as a planning tool for your next software project.
Thremo is available as a cloud based service. Because software architecture can be a sensitive topic, we will also offer a version available for offline and firm internal use.
Thremo makes it possible to collaborate with others in the design and analysis of complex architecture. In the future, it will also be able to connect to project managament tools, such as Jira.
Thremo presents the security aspects of your system in a straightforward manner - making security accessible to anyone.
Integrate Thremo into your development process from the beginning, to make security a key pillar of your project.
Thremo not only finds threats you might miss when looking at components individually - it does so way quicker than any human expert could.
Thremo follows a very straightforward, linear workflow pattern.
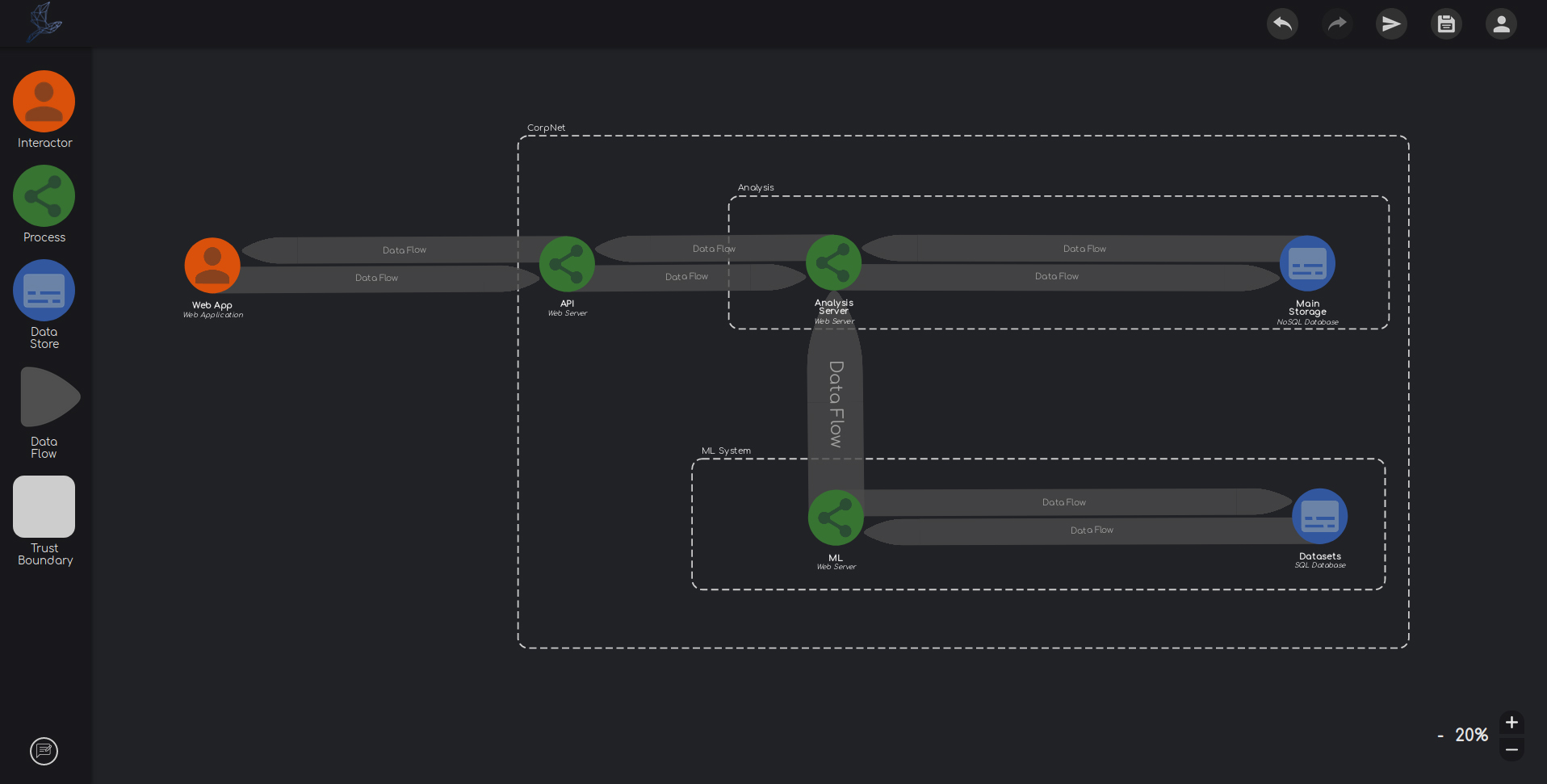
Any system can be broken down into three types of sub-components - processes, data stores, and external interactors.
Thremo follows this concept and lets you model systems of any complexity in a simple and straightforward manner. Simply drag & drop the elements on the workspace and connect them with data flows.
Thremo lets you specify each element. Properties such as the trust and privilege level not only help you think about your systems security status, but also improve the analysis.
Besides these high-level properties, you can specify software products on your elements. Thremo knows about more than 300.000 different software products, to ensure you can correctly model your system.
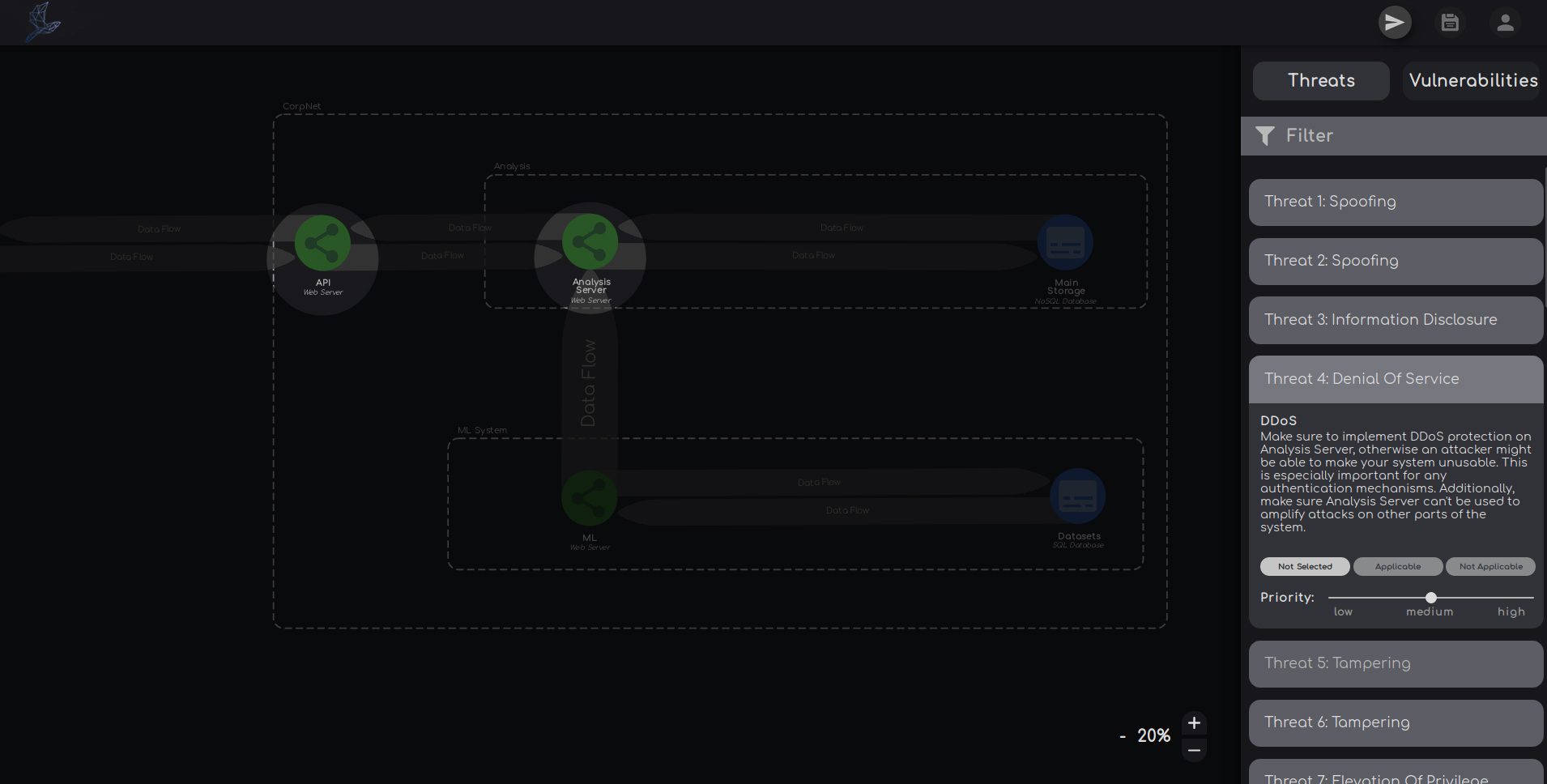
After you created a model, Thremo analyzes the data flow between each element for potential weaknesses.
Found threats describe potential risks your system might face and are meant to give you hints on which security aspects you have to think about during development. If you have specified certain software used by the elements, Thremo also returns known concrete vulnerabilities. Currently, more than 70.000 vulnerabilities are known by Thremo.
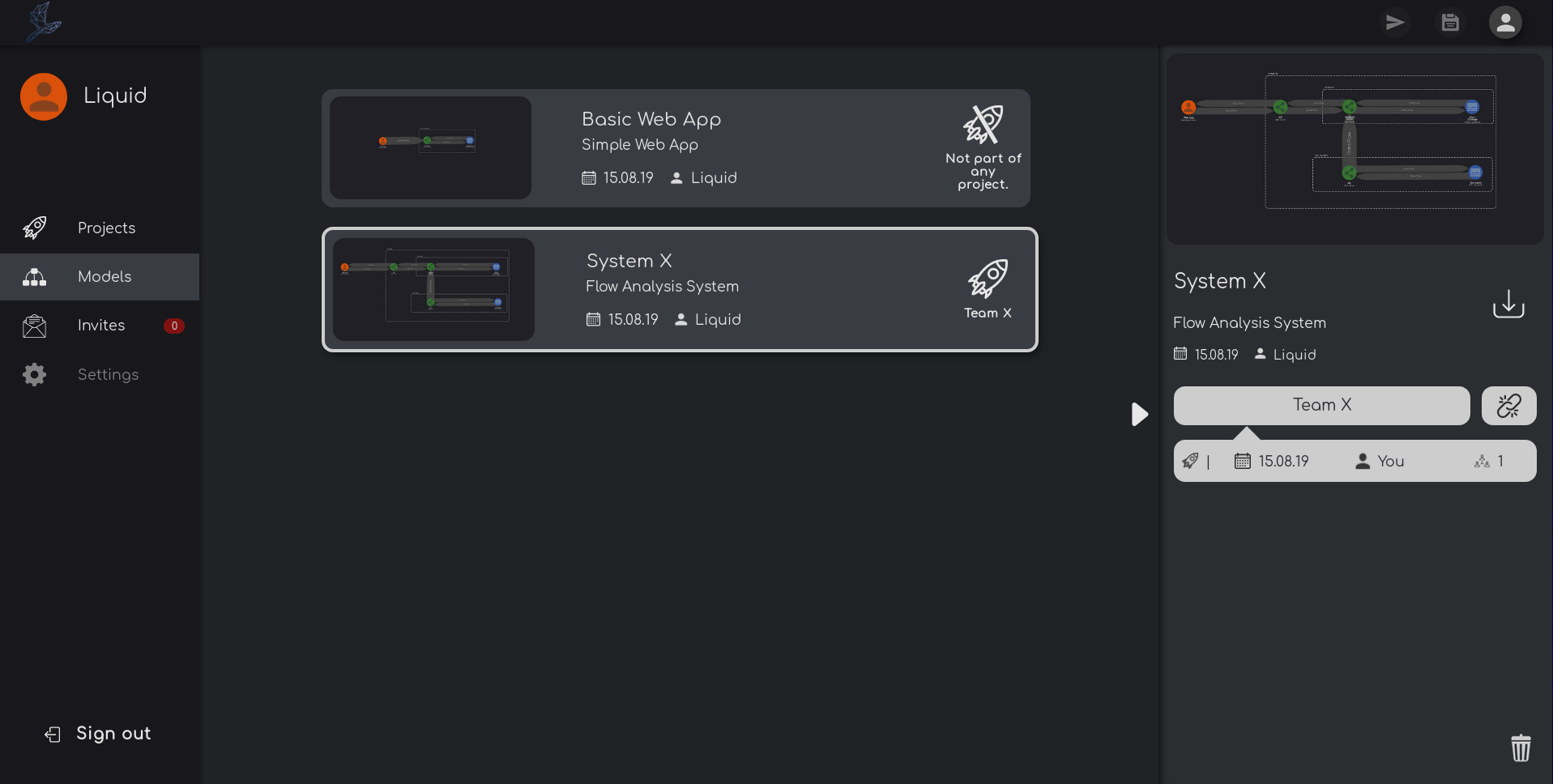
Thremo lets you store your work at any time.
Switch between different models with the click of a mouse. By making it possible to work on an unlimited amount of models, you can use Thremo for all of your projects.
Create projects to collaborate with others! Any model linked to a project can be accessed by its members.
In the future, Thremo will be able to connect to project management tools like Jira. Keep an eye out for updates!
If you have any questions, let us know! We are also looking for possible cooperations - if that sounds like something you might be interested in, we would love to get in touch with you.